Screens around the web: password restrictions
I wrote earlier about how several high profile web sites ensure that their users can NOT have strong passwords. Here are a few screen shots to prove my point:
Chase
AT&T
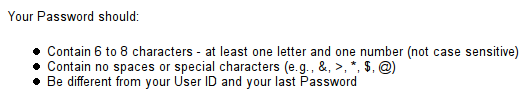
American Express
American Funds
Note that all these web sites provide financial services, and are the most dangerous to users if their accounts get hacked. Account access would in most cases make available to the hacker other personal details like credit card numbers and SSN. Some one please, PLEASE explain to me the logic behind such restrictions as putting a silly upper limit on password length (8??!! WTF!!!), and disallowing special characters. It’s retarded.
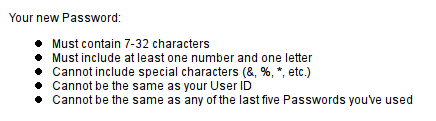
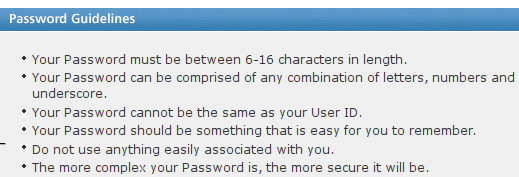

The HTTP Basic authentication scheme reserves the colon character to separate username from password. Thus a colon must not be used in the username or password. (If you know the implementation of the Basic scheme parser [indexOf(':') or lastIndexOf(':') ?], you MAY allow it in either username or password…)
I’m guessing some systems have a restriction like the above so that you can use the same password on a phone with a IVR?
but yeah.. it’s kinda silly
*@ian*: hmm, thats a good point. But still, I don’t think it quite justifies the abysmal rules. Meanwhile, have you see myvidoop.com? Quite an interesting approach to the whole password management problem.
*@odi*: So? Their software should be smart enough to escape problematic characters. In any case, no one who is serious about security would ever use HTTP Basic authentication — it is just what it says, BASIC. All of the web sites I mentioned go over HTTPS, and authentication is handled at the application layer.
Reminds me of these 2WIRE routers (i.e. EESID shows up as ###2WIRE all over town) that are set with a default password of exactly 10 numeric bytes. You can do the math… or, this is fun if perhaps somewhat spurious:
http://www.hackosis.com/projects/bfcalc/bfcalc.php
I agree completely. American Express’s restrictions in particular seem to be designed for ease of brute-forcing. There are a total of 2,684,372,063,360 possible passwords one can use with those restrictions, and I’m sure a dictionary attack program could crack the majority of their customers’ passwords in a few minutes each. Makes me want to cancel my account…
http://wondermark.com/866/